Monitoring Lab Computers with Nmap
By: James Reynolds - Revised: 2014-01-23 richardDownload Slides
–
PDF-File,
191.3 KB
Introduction
What do you get when you mix fast computers, large hard disks, lots of RAM, fast internet connections, a UNIX OS, public access to the CPU, and no monitoring? A really nice public computer lab. However, add one really smart cracker, and soon you have a really nice public lab of unauthorized internet servers.While Mac OS X is secure, it isn't impenetrable, and it is gold mine. Someday, across University campuses everywhere, really smart crackers are going to realize that cracking into convenience store safes aren't as profitable as cracking into bank vaults. When they finally realize this, it would be nice if lab admins already have security systems ready to stop them.
NMap is a tool that scans a computer's network ports. Make sure that your computers don't have network ports open that shouldn't be open by using a script and cron to automate nmap scans.
James will discuss and demonstrate automating nmap in our labs.
Section Links
Nmap
Nmap ("Network Mapper") is a free open source command line Unix utility that scans ports. The latest version is 3.48 as of Nov. 2003. It is written by "Fyodor". Some of the things Nmap can determine:What hosts are available on the network
What services and the version they are offering
What operating system and version they are running
What type of packet filters/firewalls are in use
Nmap homepage: www.insecure.org/nmap (or just www.nmap.org).
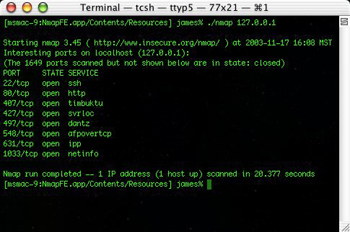
If you scan a box with Nmap, and you see an open port but don't know what it is, check these websites: If you think there is a process running on a box that shouldn't be, you need to do some forensics. See this page for some discussion about forensics.
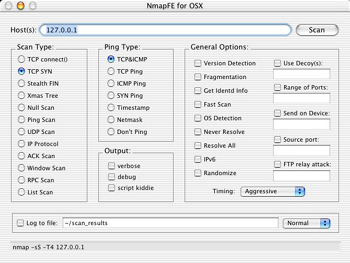
NmapFE
NmapFE is a Cocoa frontend for Nmap. Latest version is 0.80 and it includes nmap version 3.45. It is written by Matthew Rothenberg. The easiest way to get Nmap is to download NmapFE. The Nmap files are located in the NMapFE Launcher bundle at:NmapFE Launcher.app/Contents/Resources/NmapFE/Contents/Resources/nmap
NmapFE homepage: faktory.org/m/software/nmap.
Automating Nmap
Create a text file (file_with_ip_list.txt) with the ip's that you want scanned. It should look like this:10.0.1.1
10.0.1.2
10.0.1.3
10.0.1.4
10.0.1.5
10.0.1.6
10.0.1.7
10.0.1.8
10.0.1.9
10.0.1.2
10.0.1.3
10.0.1.4
10.0.1.5
10.0.1.6
10.0.1.7
10.0.1.8
10.0.1.9
etc
Make sure it has Unix line feeds. Then run this command:
Make sure it has Unix line feeds. Then run this command:
sudo /path/to/nmap -sS -sU -p 1-65535 -v -oG MyLogFile.txt -iL file_with_ip_list.txt
The above command will do a quick TCP scan of all ports (1-65535), and a slower UDP scan of all ports (1-65535). It will print verbose output, so you get alot of info. It will save the results in a grepable format in the file "MyLogFile.txt", and it will use the file file_with_ip_list.txt for the IP's scanned.
If you download NmapFE, then the path will be something like this:
NmapFE Launcher.app/Contents/Resources/NmapFE/Contents/Resources/nmap
This is kinda long. You can copy the nmap executable where ever you want, it doesn't need any of the NmapFE stuff. Take the other nmap files with it though, because nmap uses them.
There are many scanning types. I picked the -sS TCP SYN scan because it is fast. I decided to scan UDP because there are problems that can pop up there. Unfortunately, in Mac OS X 10.2 there is a range of UDP ports that like to be open and they are different on every box. I am not sure what they even are.
I picked all 65535 ports so that I know exactly what a computer is up to. I decided verbose was good to get more information.
Other than the log file and input file, I left out all other options because we don't really need to hide our scans, these are our computers after all. The only other option that needs mentioning is timing. By default it is "Normal". You can't really make it go any faster though. If you try, you will start seeing these messages in the system log of the scanned Mac:
"May 30 18:38:22 ms_osx-6 mach_kernel: Limiting closed port RST response from 318 to 100 packets per second"
If you don't want any messages in the system.log, you should slow nmap down to "Polite" or even "Sneaky", since "Normal" will generate system log messages.
If you download NmapFE, then the path will be something like this:
NmapFE Launcher.app/Contents/Resources/NmapFE/Contents/Resources/nmap
This is kinda long. You can copy the nmap executable where ever you want, it doesn't need any of the NmapFE stuff. Take the other nmap files with it though, because nmap uses them.
There are many scanning types. I picked the -sS TCP SYN scan because it is fast. I decided to scan UDP because there are problems that can pop up there. Unfortunately, in Mac OS X 10.2 there is a range of UDP ports that like to be open and they are different on every box. I am not sure what they even are.
I picked all 65535 ports so that I know exactly what a computer is up to. I decided verbose was good to get more information.
Other than the log file and input file, I left out all other options because we don't really need to hide our scans, these are our computers after all. The only other option that needs mentioning is timing. By default it is "Normal". You can't really make it go any faster though. If you try, you will start seeing these messages in the system log of the scanned Mac:
"May 30 18:38:22 ms_osx-6 mach_kernel: Limiting closed port RST response from 318 to 100 packets per second"
If you don't want any messages in the system.log, you should slow nmap down to "Polite" or even "Sneaky", since "Normal" will generate system log messages.
Parsing the output of Nmap
The first thing you have to do to get the output of Nmap is choose the output format. Nmap can output in many formats. My favorite is the "s|<ipT kiDd|3" format (the -oS flag). Other more useful formats include grepable (-oG), XML (-oX), and human readable (-oN). What you decide is up to you. Or you can use one of the Perl scripts listed below, which parse the output and prints some sort of report.nmap-audit
Nmap-audit is a Perl script that automates nmap port scans. The latest version is 1.66. It is written by Keith Resarnmap-audit homepage: heavyk.org/nmap-audit.
nmap-auto
Nmap-auto is another Perl script that automates nmap port scans, but it is a little simpler than nmap-audit.The config file contains machine profiles and the ip list. The machine profiles looks like this:
@macosx_lab {
53 udp domain
123 udp ntp
514 udp syslog
47928 udp unknown
49152-50180 udp unknown
65072-65076 udp unknown
}
@macosx_workstation {
22 tcp ssh
53 udp domain
123 udp ntp
407 udp tcp timbuktu
407 udp udp timbuktu
497 udp tcp dantz
497 udp udp dantz
514 udp syslog
1023 tcp ssh
1419 tcp timbuktu-srv3
5353 tcp ssh
12345 tcp ssh
}
@macosx_server {
22 tcp ssh
53 udp domain
68 udp dhcpclient
80 tcp http
123 udp ntp
311 tcp asip-webadmin
407 udp tcp timbuktu
407 udp udp timbuktu
497 udp tcp dantz
497 udp udp dantz
514 udp syslog
548 tcp afpovertcp
625 tcp unknown
660 tcp mac-srvr-admin
687 tcp unknown
1023 tcp ssh
1085 tcp unknown
1085 udp unknown
1220 tcp quicktime
1419 tcp timbuktu-srv3
5353 tcp ssh
12345 tcp ssh
}
53 udp domain
123 udp ntp
514 udp syslog
47928 udp unknown
49152-50180 udp unknown
65072-65076 udp unknown
}
@macosx_workstation {
22 tcp ssh
53 udp domain
123 udp ntp
407 udp tcp timbuktu
407 udp udp timbuktu
497 udp tcp dantz
497 udp udp dantz
514 udp syslog
1023 tcp ssh
1419 tcp timbuktu-srv3
5353 tcp ssh
12345 tcp ssh
}
@macosx_server {
22 tcp ssh
53 udp domain
68 udp dhcpclient
80 tcp http
123 udp ntp
311 tcp asip-webadmin
407 udp tcp timbuktu
407 udp udp timbuktu
497 udp tcp dantz
497 udp udp dantz
514 udp syslog
548 tcp afpovertcp
625 tcp unknown
660 tcp mac-srvr-admin
687 tcp unknown
1023 tcp ssh
1085 tcp unknown
1085 udp unknown
1220 tcp quicktime
1419 tcp timbuktu-srv3
5353 tcp ssh
12345 tcp ssh
}
(The above profiles are not finalized, so don't use them).
An IP list looks like this:
An IP list looks like this:
10.0.1.1 @macosx_server
10.0.1.2 @macosx_workstation
10.0.1.3-255 @macosx_lab
# etc
10.0.1.2 @macosx_workstation
10.0.1.3-255 @macosx_lab
# etc
Nmap-auto will generate 3 categories of messages: "Alert", "ALARM", and "ERROR". An open port that is listed in the profile will generate an "Alert", basically an FYI. An open port that is not listed in the profile will generate an "ALARM". If no ports are open, an "ERROR" is generated.
These messages can be saved to a log file (/var/log/nmap-auto.log) or can be sent to an administrator remotely. The current supported network reporting method is to update a FileMaker Pro database using curl. You will need to edit the included script, report_to_master.sh to customize how you want your network reports (you could even change it to email if you want).
Nmap-auto is packaged as a startup item. It will scan the computers listed on the IP list over and over. It never quits. To remove nmap-auto, remove the startup item and either restart the computer or don't remove the startup item until you type this at the command line:
These messages can be saved to a log file (/var/log/nmap-auto.log) or can be sent to an administrator remotely. The current supported network reporting method is to update a FileMaker Pro database using curl. You will need to edit the included script, report_to_master.sh to customize how you want your network reports (you could even change it to email if you want).
Nmap-auto is packaged as a startup item. It will scan the computers listed on the IP list over and over. It never quits. To remove nmap-auto, remove the startup item and either restart the computer or don't remove the startup item until you type this at the command line:
sudo SystemStarter stop nmap-auto
If you have just installed it, and you don't want to restart, you can start nmap-auto by typing in this in the Terminal:
sudo SystemStarter start nmap-auto
Download nmap-auto.pl
–
ZIP-File,
13.4 KB
- Documentation
- Administration
- Authentication
- General Software
- Hardware
- Miscellaneous
- Multimedia
- Networking
- Operating Systems
- Outside Presentations
- Programming & Scripting
- Security
- Servers
- Short Courses
- System Deployment
- System Utilities
- What's New

